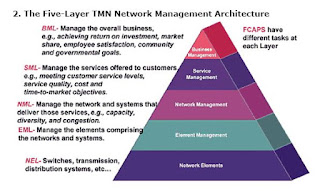
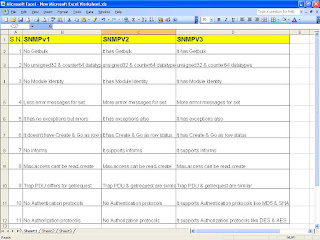
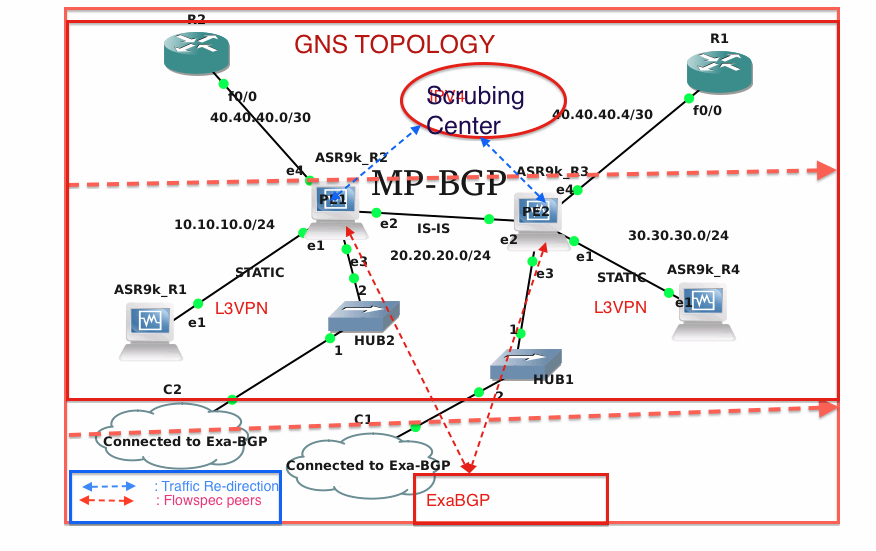
Management software solutions in the industry
Well, this article doesn’t take you into any depth of management software solutions. However, this article gives a broad insight into the current industry trends in management software solutions. When we say a management system we are using very vague term in fact. There are many different management systems to achieve different goals. As per my knowledge so far the NMS software particularly meant to manage the devices from a single vender does have most of the FCAPS functionalities in it. Which means single software is used to achieve Configuration management, performance management, fault management & monitoring, Security management & Accounting management in few cases. However, the management software which supports multiple vendors may be different for different FCAPS functionalities. Suppose one software for Network monitoring for multiple vendor NEs(ex. EMC smarts), one for Configuration management for multiple vendor NEs(Ex. HP openView), one for performance man...