DDOS Mitigation using flowspec with ExaBGP and Cisco IOS-XR routers in GNS
Introduction:
The BGP flow specification (flowspec) feature allows you to rapidly deploy and propagate filtering and policing functionality among a large number of BGP peer routers to mitigate the effects of a distributed denial-of-service (DDoS) attack over your network.
Flowspec model:
The BGP Flowspec model comprises of a Client and a Server.The Controller is responsible for sending or injecting the flowspec NRLI entry.The client (acting as a BGP speaker) receives that NRLI and programs the hardware forwarding to act on the instruction from the Controller.
In our setup, ExaBGP daemon acts as the flowspec server(Controller) and flowspec supporting cisco IOS-XR routers act as flowspec clients.
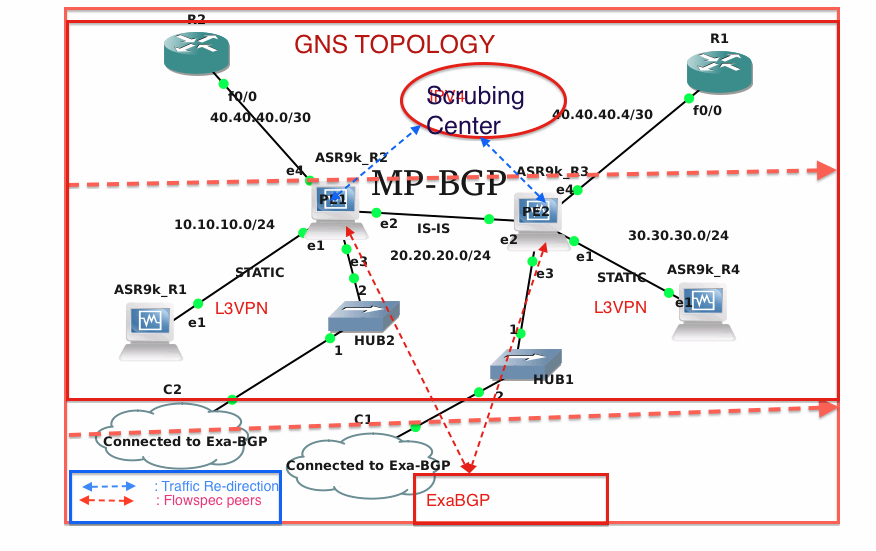
GNS topology consisting of IOS-XR routers as provider edge routers is created, and the provider edge routers are connected to the external network so that provider edge routers can talk to ExaBGP node as shown in diagram below.
Hence, ExaBGP is responsible for injecting the rules to the Provider edge routers(Flowspec client) and flowspec manager on routers is responsible for installing the rules received from ExaBGP and policy manager is responsible for applying the rules on routers based on the traffic which match the rules.
BGP flowspec configuration on clients(routers):
In bgp flowspec clients we need to enable the flowspec and configure the bgp flowspec peering with ExaBGP node. Following are the steps to perform configuration on flowspec client.
Step1: Login to router and enable flowspec
- Login to router as telnet 192.168.112.1 with password cisco/cisco
- configure t
- flowspec
- commit
- end
Step2: Configure bgp flowspec peering with exabgp node
- configure t
- router bgp
## router bgp 1 - address-family { ipv4 | ipv6 | vpnv4 | vpnv6 } flowspec ## address-family ipv4 flowspec
- exit
- neighbor
## neighbor 192.168.113.1 - remote-as
## remote-as 1 - address-family { ipv4 | ipv6 } flowspec ## address-family ipv4 flowspec
- commit
ExaBGP Setup and configuration:
ExaBGP is a tool which is designed to provide an easy way to interact with the BGP networks.It is programmed to allow the injection of arbitrary routes including ipv6 and flowspec.
Following are the steps to setup ExaBGP:
Steps1: Download and install ExaBGP
- wget https://github.com/Exa-Networks/exabgp/archive/3.4.5.tar.gz
- tar zxvf 3.4.5.tar.gz
- cd exabgp-3.4.5
- chmod +x setup.py
- ./setup.py install
- Verify the installation:
/usr/bin/exabgp --h
Step2: Configure the bgp flowspec neighbors and run exaBGP
- Prepare the configuration file as follows:
neighbor {
router-id ;
local-address;
local-as 1;
peer-as;
flow {
route {
match {
;
}
then {
;
}
}
}
}
local-address
local-as 1;
peer-as
flow {
route {
match {
}
then {
}
}
}
}
Example:
neighbor 192.168.113.1 {
router-id 192.168.112.1;
local-address 192.168.112.1;
local-as 1;
peer-as 1;
flow {
route {
match {
destination 40.40.40.0/30;
}
then {
discard;
}
}
}
}
router-id 192.168.112.1;
local-address 192.168.112.1;
local-as 1;
peer-as 1;
flow {
route {
match {
destination 40.40.40.0/30;
}
then {
discard;
}
}
}
}
- Save the configuration file as flowspec_conf.txt and run the exabgp:
env exabgp.daemon.daemonize=true /usr/bin/exabgp
Example: env exabgp.daemon.daemonize=true /usr/bin/exabgp /data/exabgp/configs/flowspec_conf.txt
Dynamic flowspec rules injection via ExaBGP:
Instead of injecting the static flowspecs rules, we need to inject flowspecs rules dynamically without peering down the connection.For this we can leverage the multithreading functionality of ExaBGP.
ExaBGP launch a process for establishing the peering and also it forks the separate process for injecting the rules dynamically.
Here is the detailed procedure:
Step1: Prepare the flowspec configuration file as follows:
neighbor 192.168.153.68 { ## This is your flowspec neighbor router.
router-id 192.168.112.140; ## This is the ExaBGP node IP
local-address 192.168.112.140;
local-as 1;
peer-as 1;
process service-dynamic {
run /data/Indu/exabgp-3.4.5/etc/exabgp/processes/dynamic.sh; ## the script which contains the flows to anounce/withdraw
}
}
Here is the content of /data/Indu/exabgp-3.4.5/etc/exabgp/processes/dynamic.sh
#!/bin/sh
# ignore Control C
# if the user ^C exabgp we will get that signal too, ignore it and let exabgp send us a SIGTERM
trap '' SIGINT
# if the user ^C exabgp we will get that signal too, ignore it and let exabgp send us a SIGTERM
trap '' SIGINT
# command and watchdog name are case sensitive
while `true`;
do
echo "announce flow route {\\n match {\\n source 40.40.40.1/32;\\n destination 40.40.50.1/32;\\n }\\n then {\\n discard;\\n }\\n }\\n"
sleep 10
echo "announce flow route {\\n match {\\n source 80.80.80.1/32;\\n destination 80.80.80.1/32;\\n }\\n then {\\n discard;\\n }\\n }\\n"
do
echo "announce flow route {\\n match {\\n source 40.40.40.1/32;\\n destination 40.40.50.1/32;\\n }\\n then {\\n discard;\\n }\\n }\\n"
sleep 10
echo "announce flow route {\\n match {\\n source 80.80.80.1/32;\\n destination 80.80.80.1/32;\\n }\\n then {\\n discard;\\n }\\n }\\n"
done
Step2: Run ExaBGP with the configuration file prepared above
/data/Indu/exabgp-3.4.5/sbin/exabgp /data/Indu/exabgp-3.4.5/etc/exabgp/flowspec_conf_dynamic.txt
With above two steps flowspec peering is established. To inject more flowspec rules in incremental basis without peering down the neighbors perform following steps:
Step3: Add new flowspec rule in dynamic.sh script
Add the flow spec rule as:
echo "announce flow route {\\n match {\\n source 90.90.90.1/32;\\n destination 90.90.80.1/32;\\n }\\n then {\\n discard;\\n }\\n }\\n"
Step4: Find the forked process id for dynamic.sh script & kill it
[root@BR-140 configs]# ps -aef | grep -i bgp | grep -v grep
nobody 19576 9574 0 10:53 pts/38 00:00:01 /usr/bin/python2.6 /data/Indu/exabgp-3.4.5/lib/exabgp/application/bgp.py --folder /data/Indu/exabgp-3.4.5/etc/exabgp /data/Indu/exabgp-3.4.5/etc/exabgp/flowspec_conf_dynamic.txt
nobody 30642 19576 0 10:55 pts/38 00:00:00 /bin/sh /data/Indu/exabgp-3.4.5/etc/exabgp/processes/dynamic.sh
nobody 30642 19576 0 10:55 pts/38 00:00:00 /bin/sh /data/Indu/exabgp-3.4.5/etc/exabgp/processes/dynamic.sh
& run kill -9 ## kill -9 30642
Step5: Check that newly added flowspec rule is added to the router without peering down the connections
RP/0/0/CPU0:ios#show flowspec ipv4
Fri Jan 9 10:31:51.984 UTC
Fri Jan 9 10:31:51.984 UTC
AFI: IPv4
Flow :Dest:1.1.1.1/32
Actions :Traffic-rate: 0 bps (bgp.1)
Flow :Dest:40.40.50.1/32,Source:40.40.40.1/32
Actions :Traffic-rate: 0 bps (bgp.1)
Flow :Dest:90.90.80.1/32,Source:90.90.90.1/32
Actions :Traffic-rate: 0 bps (bgp.1)
Flow :Dest:1.1.1.1/32
Actions :Traffic-rate: 0 bps (bgp.1)
Flow :Dest:40.40.50.1/32,Source:40.40.40.1/32
Actions :Traffic-rate: 0 bps (bgp.1)
Flow :Dest:90.90.80.1/32,Source:90.90.90.1/32
Actions :Traffic-rate: 0 bps (bgp.1)
RP/0/0/CPU0:ios#show bgp ipv4 flowspec sum | begin Neighbor
Fri Jan 9 10:33:50.636 UTC
Neighbor Spk AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down St/PfxRcd
192.168.112.140 0 1 200 161 49 0 0 00:20:52 3
Fri Jan 9 10:33:50.636 UTC
Neighbor Spk AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down St/PfxRcd
192.168.112.140 0 1 200 161 49 0 0 00:20:52 3
Above checks proves that new flowspec rules are injected without peering down the connections
Verification of flowspec setup:
Following are the few steps(but not limited to) to verify the flowspec setup:
Step1: Verify that sockets are up on exaBGP server.
Step2: Run following commands in flowspec routers verify flowspec peering.
- show processes flowspec_mgr location all
- show flowspec summary
- show flowspec vrf vrf_name | all { afli-all | ipv4 | ipv6}
- show bgp ipv4 flowspec
Step3: Transmit data(telnet,ping,tftp etc) which matches the configured flowspec rule for the data entering into flowspec router and check the action taken by rules. In this example, telnet from ASR9k_R4 to ASR9k_R1 or telnet from R1 to R2.
Comments
I am working on a project in my company need your help.Please contact me on postme.imran at gmail dot com
No ASR9k needed huh ?
https://www.linkedin.com/pub/amit-singh/54/747/5b7
To integrate GNS with exabgp, follow the following steps:
1. First connect one of you GNS router to Cloud via your physical interface such as eth0.
2. Add route in the GNS router to reach to the network your server resides. Make sure the gateway address is the one same as that of server where GNS software resides.
3. Install exabgp in a server for which route from GNS router is configured.
4. By this time, you should be able to communicate Server & GNS router.
5. run exabgp to peer with GNS router IP.
Hope it helps.
To integrate GNS with exabgp, follow the following steps:
1. First connect one of you GNS router to Cloud via your physical interface such as eth0.
2. Add route in the GNS router to reach to the network your server resides. Make sure the gateway address is the one same as that of server where GNS software resides.
3. Install exabgp in a server for which route from GNS router is configured.
4. By this time, you should be able to communicate Server & GNS router.
5. run exabgp to peer with GNS router IP.
Hope it helps.